Cyber extortion is a form of cybercrime where attackers threaten to damage, disable, or release a victim’s digital assets, such as data, systems, or networks, unless a ransom is paid or a demand met. These crimes are becoming increasingly frequent and costly. Read on to learn what cyber extortion is, how it works, and what you can do to be prepared.
Cyber Extortion
What is it?
Cyber extortion is a criminal act in which attackers use digital threats to demand money or specific actions from a victim, often under the threat of harming or exposing sensitive digital assets. These assets may include data, networks, computer systems, or applications. Unlike traditional extortion where threats might involve physical property or personal harm, cyber extortion operates entirely in the digital realm. Instead of threatening to burn down a storefront, for example, cybercriminals may threaten to delete critical data, leak confidential information, or disrupt operations unless a ransom is paid. Tactics include ransomware (which encrypts data), data leak threats, DDoS-for-ransom attacks, and other malicious activities that hold a business’s digital infrastructure hostage.
For the criminal, the goal is to pressure the victim into payment by threatening serious operational, financial, or reputational harm. Common threats include locking users out of their systems, publishing sensitive customer or employee information, inserting malicious code into digital environments, or slowing down platforms critical to business continuity. In many cases, these attacks are timed for maximum disruption, such as during peak sales periods or following high-profile announcements.
Costs of an attack
The actual cost to a victim of a cyber extortion incident can be massive. Typically costs include not only a ransom payment (if made), but also business downtime, loss of sales, legal fees, crisis management fees, recovery costs, and potentially, lawsuits, regulatory penalties, and more. The NetDiligence Cyber Claims Study 2024 report found an average total incident cost of US$432,000 for the small and medium sized enterprises (n=2580) that reported ransomware incidents. Hardly a small sum for an SME, and that is for just one type of cyber extortion. Every year organizations lose billions to cyber extortion as malicious actors increasingly targeted organizations of all sizes, holding their digital operations hostage.
How does cyber extortion work?
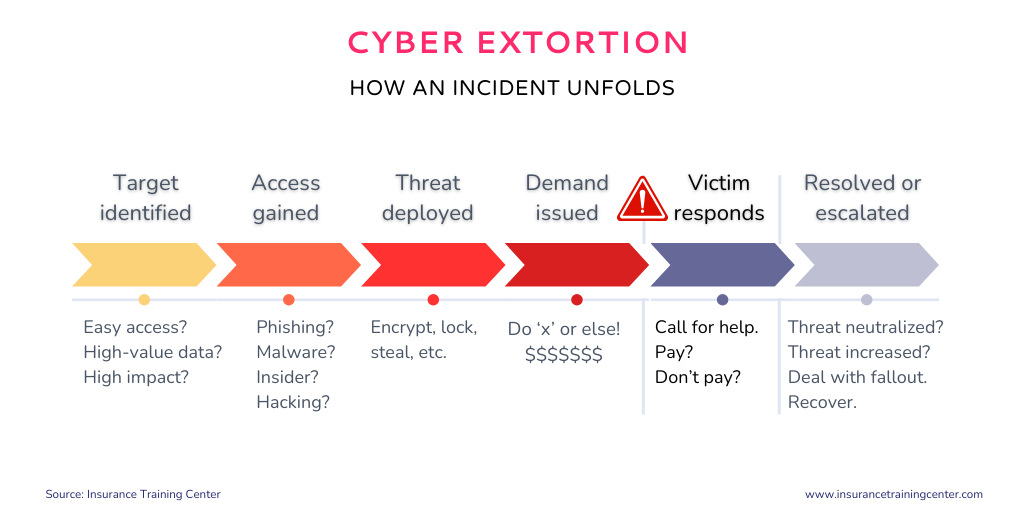
A cyber extortion incident typically begins with the attacker identifying a vulnerable target, often a business with sensitive data or critical operations. Next, they gain access through methods like phishing, malware, or exploiting security flaws. Once inside, the attacker may encrypt files (ransomware), steal data, or disrupt services. They then issue a demand—often with proof of access—requiring payment, typically in cryptocurrency, in exchange for restoring access or not leaking information.
Victims must quickly respond by advising their insurer, assessing the threat, involving legal and cybersecurity experts, and notifying law enforcement. If they pay the ransom, attackers may or may not fulfill their promise. If not, they may escalate the attack or publish stolen data. Recovery involves restoring systems, investigating the breach, and managing reputational or legal consequences. Cyber extortion insurance can help cover ransom payments, business interruption losses, and response costs.
Cyber extortion vs. ransomware
Often the terms ‘cyber extortion’ and ‘ransomware’ are used interchangeably. Doing so is missleading and here is why:
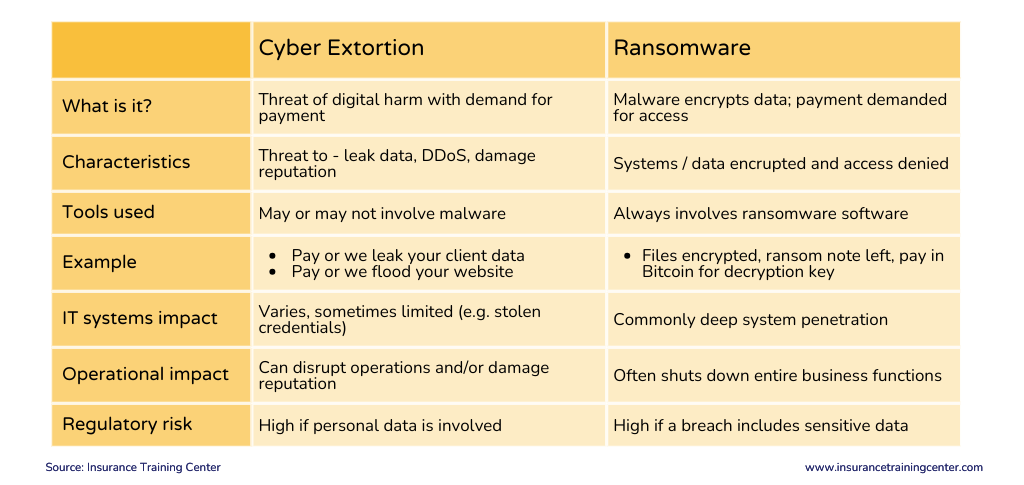
‘Cyber extortion’ is a broad category of cybercrime involving threats to damage, disrupt, or expose digital assets unless a ransom or demand is met. It includes a range of tactics such as threats to leak stolen data, launch DDoS attacks, or publicly embarrass an organization. These attacks may or may not involve malware, and they aim to pressure victims through fear, urgency, or reputational harm. Cyber extortion can occur without disabling systems, making it a versatile and often more psychological form of cyberattack.
Ransomware, on the other hand, is a specific type of cyber extortion that uses malware to encrypt or lock a victim’s files or systems. The attacker then demands payment, typically in cryptocurrency, for a decryption key to restore access. While ransomware is one of the most common and destructive forms of cyber extortion, it represents only one tactic within the broader threat category. All ransomware is cyber extortion, but not all cyber extortion involves ransomware.
Common types of cyber extortion
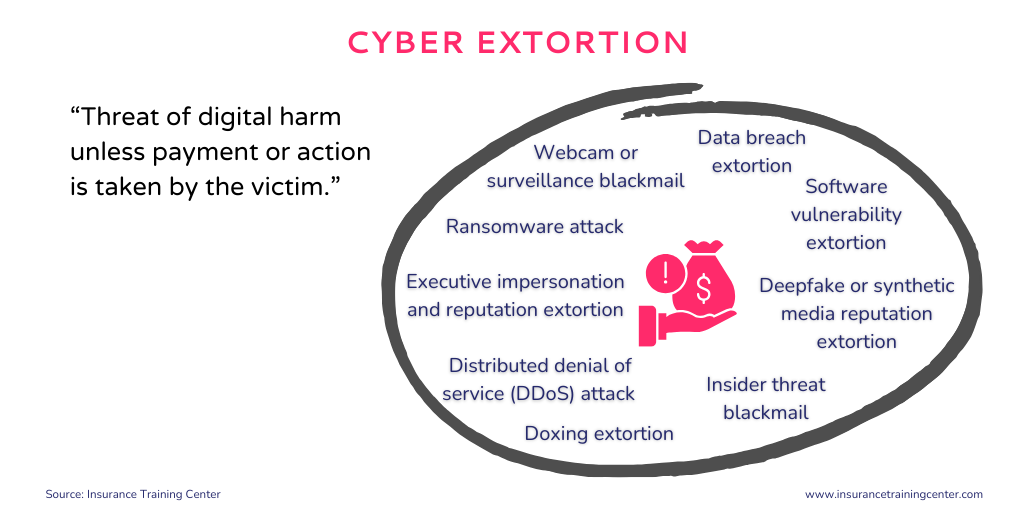
Extortion is like a tool in a toolbox. Cybercriminals use it many different ways, in a variety of situations, and are always finding new uses. While ransomware may be the crime most talked about, below are some other common types. Note, this list is not exhaustive nor set, as crime is continually evolving. The bottomline is that they all threaten to cause some sort of digital harm if the victim does not take a specific action, typically, a payment.
Data Breach Extortion – Threatening to leak stolen sensitive data unless a ransom is paid.
Deepfake or Synthetic Media Reputation Extortion – Using AI-generated images, video, or audio to fabricate compromising content and demand payment to suppress it.
Distributed Denial of Service (DDoS) Attack – Threatening or launching a website/system overload unless paid to stop or prevent it.
Doxing (Doxxing) Extortion – Threatening to publicly release personal or private information to intimidate or coerce.
Executive Impersonation and Reputation Extortion – Pretending to be a company leader to spread false or damaging information unless demands are met.
Insider Threat Blackmail – Employee or contractor uses internal access to threaten exposure or disruption unless compensated or appeased.
Ransomware Attack – Using malware to encrypt data or systems then demand payment for a decryption key.
Software Vulnerability Extortion – Exploiting or threatening to expose a flaw in software unless paid to remain silent.
Webcam or Surveillance Blackmail – Using compromised camera footage to threaten privacy invasion unless payment is made.
Protecting your organization
Cybercriminals can strike without warning, causing serious operational, financial, and reputational harm. Keeping your IT systems and cybersecurity measures up-do-date and ensuring redundancy is a given. So is the need for well rehearsed response and recovery plans. But preparation should go further than that. Being well prepared requires a broad strategy that reduces your organization’s exposure, ensure quick recovery, and limit loss. Here’s how to build effective protection:
Preparation and risk management
Strengthen your organization’s guard against attacks and minimize the potential loss should you become a victim.
- Understand your organization’s unique cyber risk landscape.
- Identify your most valuable digital assets (e.g., customer data, financial systems).
- Assess how vulnerable those assets are to extortion-related threats.
- Evaluate the potential financial, legal, and reputational cost of an attack.
- Conduct regular cyber risk assessments and vendor evaluations.
- Establish baseline cybersecurity standards and enforce them consistently.
- Build a cybersecurity-aware culture across all levels of the organization.
- Treat cybersecurity as a strategic business priority, not just an IT issue.
Insurance considerations
A prudent organization has cyber extortion insurance coverage in place to help absorb some of the costs and limit the financial and other damage to the organization should an incident occur.
- Review your insurance for cyber extortion coverage (or “extortion threat coverage”)
- Understand what’s included and excluded; especially limits, ransom conditions, and cryptocurrency restrictions.
- Learn about your insurance options, what else is available on the market?
- Confirm whether the policy includes incident response services like IT forensics, legal counsel, and breach response teams.
- Ensure the policy you choose aligns with your organization’s specific digital risks.
Key takeaways
- Cyber extortion is a cybercrime in which attackers threaten to damage, disable, or release a victim’s digital assets (such as data, systems, or networks) unless a ransom is paid.
- There are many different forms of cyber extortion. Ransomware is just one example.
- Important to fully understand and manage your organization’s risk.
- Cyber extortion insurance helps limit loss from an incident.
More…